Wire and ACH fraud is on the rise. It is possible you and your company have already experienced it, or you know someone that it happened to, or you have read stories about it. The question to be asked is: “Why wait for this to happen to you or your company (possibly again) to take a few measures that can reduce your chances of significant loss of money and the resulting business disruption?”
Wire and ACH Fraud Defined
Wire and ACH fraud involve the unauthorized transfer of money from a bank account using an Electronic Funds Transfer (“EFT”). Wire transfers allow for money to move directly from one bank account to another bank account. ACH transfers use the Automated Clearing House (“ACH”) Network that is governed by the National Automated Clearing House Association (“Nacha”). Nacha has defined standards to reduce fraud when sending payments through the ACH Network.
Wire and ACH fraud can occur through the following two methods: 1) undetected account takeover or 2) unknowing participation. Undetected account takeover results when a cybercriminal (or “scammer”) obtains your login credentials to your bank account and is then able to initiate and process unauthorized EFTs. Unknowing participation occurs when a cybercriminal tricks an authorized bank account owner to login to their bank account and send an EFT to the bank account of the cybercriminal, thinking that the cybercriminal is a legitimate, correct recipient of the funds.
Typical Methods Used by Cybercriminals
Cybercriminals can be anyone, like your neighbor, or they can be located anywhere in the world, and they can be of any age or nationality. Wire and ACH fraud is growing because it’s proven to be easy for cybercriminals to achieve their objective – stealing money. The tools scammers use are readily available on the internet (some for free and some for a fee). Cybercriminals are getting more creative every day and their reach is global. They use the following methods to gain the information they need from you to carry out their criminal activities:
Phishing: The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.1
Spear Phishing: The fraudulent practice of sending emails ostensibly from a known or trusted sender in order to induce targeted individuals to reveal confidential information.1
Smishing: The fraudulent practice of sending text messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords or credit card numbers.1
Vishing: The fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as bank details and credit card numbers.1
Malware: Short for “malicious software”, is a file or code, typically delivered over a network, that infects, explores, steals or conducts virtually any behavior an attacker wants. And because malware comes in so many variants, there are numerous methods to infect computer systems. Though varied in type and capabilities, malware usually has one of the following objectives:
Regarding spear phishing, scammers are more frequently taking advantage of publicly available information on social media (Meta, Twitter, LinkedIn, etc.) to increase the number of successful attacks. For example, scammers may see that you recently were in Italy, and when sending a spear phishing email, may say “Hope you had a nice time in Italy.” A message like that helps to lower your guard and increase the chances that you believe the email is from a legitimate source, which then sends you on the path toward sending an EFT to the scammer.
For malware, once the scammer obtains your login credentials, they can initiate and process EFTs without your approval (depending on the controls that you may have implemented as discussed below).
Example Emails Used for Wire/ACH Fraud
If you remain skeptical and learn about how cybercriminals think, you’ll be able to more easily identify the details of an email that are indicators of a scam.
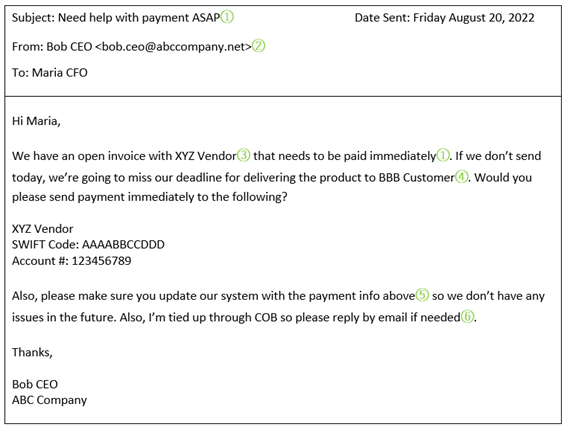
| Executive Management and Internal Employee Spoofing | ||
|
(1) Sense of urgency detracts you from investigating this request.
(2) Incorrect email domain address can easily be over-looked.
(3) Scammer obtained a valid vendor name through one or more of the methods discussed above.
(4) Scammer obtained a valid customer name through one or more of the methods discussed above.
(5) Should never use or update payment information without initiating your own call or email from your own source (not responding to a call or email received).
(6) Another indicator of fraud when email directs you to respond only as told. |
 |
|
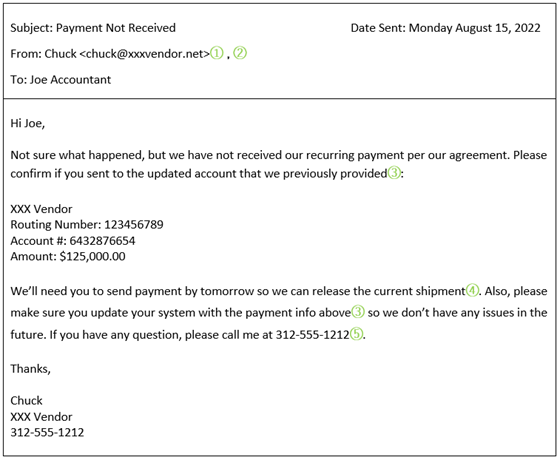
| Vendor Spoofing | ||
|
(1) Scammer obtained a valid vendor name through one or more of the methods discussed above.
(2) Vendor’s domain is not correct, so Chuck will not receive replay email.
(3) Should never use or update payment information without initiating your own call or email from your own source (not responding to a call or email received).
(4) Sense of urgency detracts you from investigating this request.
(5) Another indicator of fraud when email directs you to respond by a certain method. |
 |
|
The 5 Steps to Reduce Your Chances of Wire/ACH Fraud
An effective cybersecurity program requires the proper harmonization of people, processes, and technology along with a company culture that emphasizes security. Implementing the appropriate processes, controls, policies, and potentially new technology has associated costs. If your budget does not allow for a comprehensive cybersecurity program, then you may want to consider implementing targeted controls to certain areas. Using wire and ACH fraud as an example, companies can easily implement the following steps to manage the risk of losing money from unauthorized EFTs.
(1) Never send a wire or ACH from a request that came in by phone (call or text) or email. Use your own contact information and reach out to someone you know (at your own company or at the vendor) to confirm the requested payment and related bank account information. A phone call is better than email since you should be able to confirm the voice of your contact.
(2) Setup your online banking to require a second person to approve wires and ACH’s. Also, if you think this is already setup, I suggest you verify with your bank as I’ve seen miscommunication on this account configuration.
(3) Never log into your online bank account from a device (e.g., laptop) that is not your own, or is connected to the internet by a public Wi-Fi.
(4) Designate one computer, or a limited number of computers, to be used exclusively for financial transactions, and not for other activities (e.g., surfing the internet or receiving email).
(5) Implement controls to ensure that all your company’s computers are setup to install operating system patches and antimalware updates automatically when available from the software vendors. All computers should be updated, but especially the computers used to process EFTs.
If a computer is connected to the internet, there is never any way to eliminate the various risks. However, the 5 steps above will go a long way to managing risk of wire and ACH fraud to a level that should significantly reduce your chances of unauthorized outbound EFTs.
For additional steps that you may want to consider for protecting your company from wire and ACH fraud, or if you’d like to discuss a comprehensive cybersecurity program, please contact Michael Becker.
1https://languages.oup.com/google-dictionary-en/
2https://www.paloaltonetworks.com/cyberpedia/what-is-malware
The summary information in this document is being provided for education purposes only. Recipients may not rely on this summary other than for the purpose intended, and the contents should not be construed as accounting, tax, investment, or legal advice. We encourage any recipients to contact the authors for any inquiries regarding the contents. FGMK (and its related entities and partners) shall not be responsible for any loss incurred by any person that relies on this publication.
About FGMK
FGMK is a leading professional services firm providing assurance, tax and advisory services to privately held businesses, global public companies, entrepreneurs, high-net-worth individuals and not-for-profit organizations. FGMK is among the largest accounting firms in Chicago and one of the top ranked accounting firms in the United States. For over 50 years, FGMK has recommended strategies that give our clients a competitive edge. Our value proposition is to offer clients a hands-on operating model, with our most senior professionals actively involved in client service delivery.